You need to have rights to configure certain things in Microsoft Azure when you are setting it up for the first time. I will list those three permissions and the reasons for them in this post.
1. Global Admin Rights
You are going to need rights to configure things in Azure AD. For example, you should be creating security groups and using those for role-based access control of things like management groups, subscriptions, and maybe even resource groups – the higher in the hierarchy, the better, in my opinion.
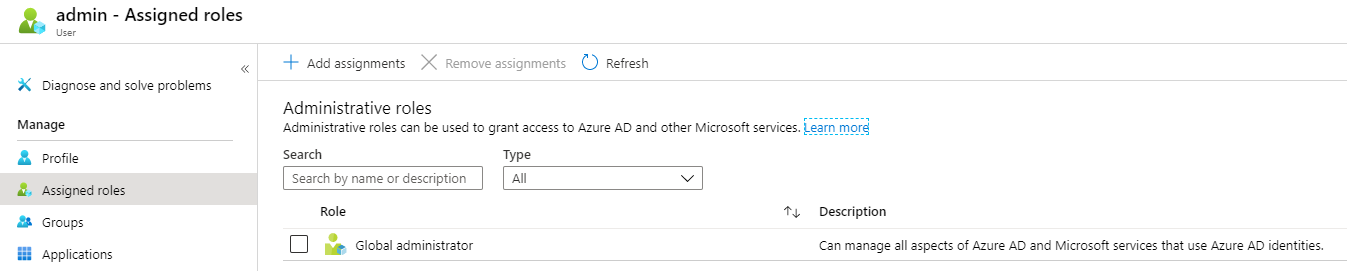
This will require that you have Global Admin Rights. This is the equivalent of being a domain admin in Azure AD, and will impact all services attached to your directory such as Office 365. This right should be limited to just a few people. In a very large organisation, someone else might be doing these tasks for you because you will not be granted the necessary rights.
This role is easily added to the user account in Azure AD, either at the time of creation or later by opening the user account and selecting Assigned Roles.
2. Access Management For Azure Resources
This is an easy right to miss! It is also known as Elevated Access. This right gives you access to all subscriptions and management groups in your directory (tenant) and therefore grants you superuser powers that should be limited to a very small group of capable people. Here’s how I learned about the right: I was cleaning up management groups that I created using a service principal. I knew the management groups were there, and I could see them, but my Global Admin user couldn’t remove them. It was only when I elevated my account that I was able to move the subscriptions and remove the management groups.
Part of the reason this right is so hidden is that it is not configured in the user account screen in the Azure Portal. Instead, sign in to the Portal with your Global Admin-enabled user, open Azure AD, and then go to Properties. Now click “Yes” under Access Management For Azure Resources. Now you will have rights to everything in Azure even if you weren’t granted them originally – this is why this superpower should be tightly controlled!
3. Role-Based Access
The typical person working with Azure should have only the rights that they need to do their job. The two big reasons are:
- External threats: Prevent someone from compromising a dev/ops employee’s account and using their rights to compromise the entire system.
- Internal threats: Limit access that a single employee has, either for security or compliance reasons.
For example, one should not be made a subscription owner just “because”. Typically, being made a Contributor will give you more than enough rights to do your job in a subscription. And maybe a lesser right is necessary – an auditor might only be made a Reader or you might use/create a more specialised role.
One should start the RBAC design using management groups. As with organisational units in Active Directory Domain Services, management groups should model the administrative model, not the HR org chart. Permissions and policy association should start at the top and become more granular as you work your way down. Eventually, you will grant dev/ops rights often at the subscription or even resource group level.
Another Consideration: Privileged Identity Management
PIM is a solution in the Azure AD per-user licensing SKUs that is sometimes used in large enterprises. It allows you to deploy just-in-time access to Azure resources/rights. There are a bunch of features in PIM that make it a useful feature to limit any one person’s access to what they need, when they need it, and for only as long as they need it, with MFA, oversight, and auditing.