In this post, I will discuss how the DNS features, DNS Servers and DNS Proxy, can be used to enable FQDN-based rules in the Azure Firewall.
Can’t Azure Firewall Already Do FQDN-based Rules?
Yes – and no. One of the rules types is Application Rules, which control outbound access to services which can be based on a URI (a DNS name) for HTTP/S and SQL (including SQL Server, Azure SQL, etc) services. But this feature is not much use if:
- You have some service in one of your VNets that needs to make an outbound connection on TCP 25 to something like smtp.office365.com.
- You need to allow an inbound connection to an FQDN, such as a platform resource that is network-connected using Private Endpoint.
FQDN-Based Network Rules
Network rules allow you to control flows in/out from source to destinations on a particular protocol and source/destination port. Originally this was, and out of the box this is, done using IPv4 addresses/CIDRs. But what if I need to have some network-connected service reach out to smtp.office365.com to send an email? What IP address is that? Well, it’s lots of addresses:
nslookup smtp.office365.com
Non-authoritative answer:
Name: DUB-efz.ms-acdc.office.com
Addresses: 2603:1026:c02:301e::2
2603:1026:c02:2860::2
2603:1026:6:29::2
2603:1026:c02:4010::2
52.97.183.130
40.101.72.162
40.101.72.242
40.101.72.130
Aliases: smtp.office365.com
outlook.office365.com
outlook.ha.office365.com
outlook.ms-acdc.office.com
And that list of addresses probably changes all of the time – so do you want to manage that in your firewall(s) rules and in the code/configuration of your application? It would be better to use the abtsraction provided by the FQDN.
Network Rules allow you to do this now, but you must first enable DNS in the firewall.
Azure Firewall DNS
With this feature enabled, the Azure Firewall can support FQDNs in the Network Rules, opening up the possibility of using any of the supported protocol/port combinations, expanding your name-based rules beyond just HTTP/S and SQL.
By default, the Azure Firewall will use Azure DNS. That’s “OK” for traffic that will only ever be outbound and simple. But life is not normally that simple unless you host a relatively simple point solution behind your firewall. In reality:
- You might want to let on-premises/remote locations connect to Private Endpoint-enabled PaaS services via site-to-site networking.
- You might hit an interesting issue, which I will explain in a moment.
Before I move on, for the Private Endpoint scenario:
- Configure DNS servers (VMs) on you VNet configuration
- Configure conditional forwarders for each Private Endpoint DNS Zone to forward to Azure Private DNS via 168.63.129.16, the virtual public IP address that is used to facilitate a communication channel to Azure platform resources.
- Set the Azure Firewall DNS Server settings to point at these DNS servers
- Route traffic from your site-to-site gateway(s) to the firewall.
Split DNS Results
If two different machines attempt to resolve smtp.office365.com they will end up with different IP addresses – as you can see in the below diagram.
The result is that the client attempts to connect to smtp.office365.com on IP address A, and the firewall is permitting access on IP address B, so the connection attempt is denied.
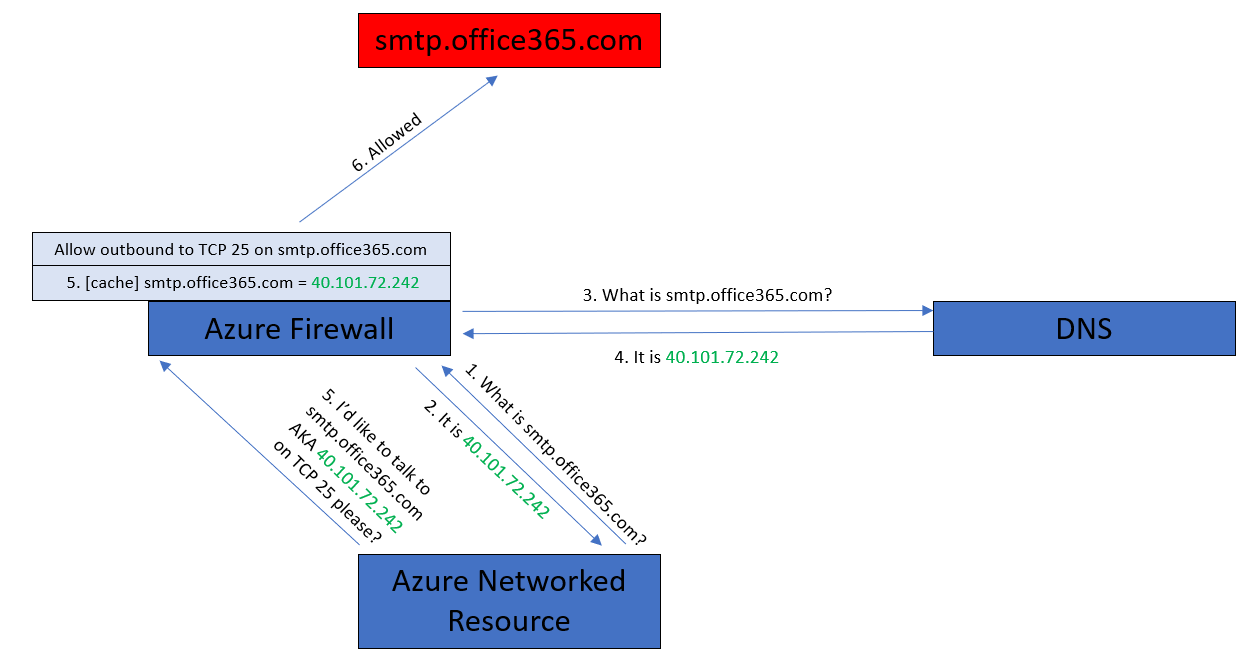
DNS Proxy
To overcome this split DNS result (the Firewall and client getting two different resolved IP addresses for the FQDN) we can use DNS Proxy.
The implementation is actually pretty simple:
- Your firewall is set up to use your preferred DNS server(s).
- You enable DNS Proxy (a simple on/off setting).
- You configure your VNet/resources to use the Azure Firewall as their DNS server.
What happens now? Every time your resource attempts to resolve a DNS FQDN, it will send the request to the Azure Firewall. The Azure Firewall proxies/relays the request to your DNS server(s) and waits for the result which is cached. Now when your resource attempts to reach smtp.office365.com, it will use the IP address that the firewall has already cached. Simples!
And yes, this works perfectly well with Active Directory Domain Controllers running as DNS servers in a VNet or spoke VNet as long as your NSG rules allow the firewall to be a DNS client.