Volume 13 (Jan-June 2012) of the Microsoft SIR has been released. Last year I read the same one, and Conficker was still the number 1 malware on domain-joined computers. What nuggets are there this year?
Before we get there …
I heard of another report (Symantec I think) that a new kind of attack is being employed by hackers called a “water-hole attack”. Much like Lions on the plains, the hackers lie in wait at locations where their prey comes to get something. So they deliberately place targeted malware on a site that they know their intended victim will visit, and wait. And eventually *bang* they hit and take over a machine in the networks of their victim. It’s more efficient than the normal un-targeted drive-by attack.
Hackers are also now attacking the supply chains of their prey. This is a good approach if you wanted to cripple a manufacturer, e.g. hit their suppliers so the manufacturer cannot produce. This is very effective now because of Just-in-Time manufacturing and exclusive supply contracts. The real victim (the manufacturer) can do nothing with their own IT security to defend against this. The only solutions are business ones: demand high levels of security/compliance in suppliers, and have varied supply chains so one down supplier does not shut down the business.
And back to the main event …
Unsecure Supply Chains
There is a rise in malware being spread by BitTorrent, warez, legit website downloads, etc. The rise in BYOD and consumerisation of IT makes this a threat in the business. Users are downloading software outside of the traditional locked down administrator-driven controls, and they are bringing in malware.
Win32/Keygen is a common threat in this space, and the name gives away what it sells itself as – a quick way to activate software that you haven’t bought or can’t find a product key for: Photoshop, Nero, AutoCAD, Call of Duty, etc. Some “Adobe Flash” installers were also found with malware. These were non legit installers hosted on 3rd party sites; the user comes to a site that won’t play and they’re told to install an up to date version of Flash. They do, and their PC is owned, because that was not the official installer from the Adobe site.
Contrary to many misconceptions, no malware can offer 100% protection anymore. There are just too many attacks, many of which go unreported for very long times thanks to the new zero-day black markets and their “royalty for staying quiet” payment schemes. The days of the teenager in the basement are over, and this stuff is very professional now, looking to steal confidential data and financial access.
What can help is a well designed BYOD scheme with isolation. I like the App Catalog in ConfigMgr 2012. It gives the user the flexibility of BYOD but on a corporate machine. As for true, BYPD personally owned devices, you have to treat those as untrusted and not let them all the way in, in my opinion. Windows To Go is a nice touch, allowing the user to use their own device but they must use a Windows 8 image on a USB 3.0 storage device that is provided and managed by the business.
This kind of malware is a real threat in BYOD deployments. Isolate those machines and only give them limited access to web apps via firewalls is my thinking. But I can see how that’s not enough, e.g. key loggers.
Microsoft has a few suggestions:
- Acceptable usage policies: sorry, but users are stupid (rule #1) and rules are made to be broken. We all know that IT only creates these policies to make life more intolerable anyway – that was sarcasm, by the way. Blocking and limited rights are the only way forward.
- Block P2P: That goes without saying for LAN/Internet access but is a challenge for mobile computing, without expensive 3rd party software
- Procurement: Buy all hardware and image for the users … hmm
- Use AppLocker: Software Assurance required for this white listing solution on Windows 7/8 Enterprise
- Use a 64-bit OS: Not a solution but it appears to limit success of attacks.
Windows To Go or RDS/Citrix seems like the solution for BYOD to me. Let them use the device of their choice, but not the OS/data on that machine.
Disclosed Vulnerabilities
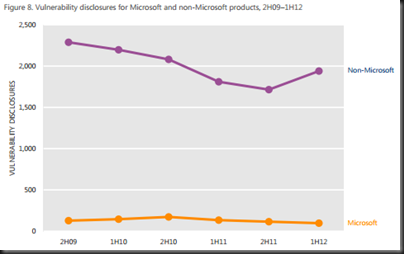
This refers to the number of industry revealed weaknesses in software. There had been a trend where this number was dropping from 2009 to 2011, but we see a rise in 2012, across low, medium, and high risk threats. 50% of threats in H1 2012 where medium and 31.5% were high risk.
OS vulnerabilities have been dropping since 2010 and continue to do so. Browser vulnerabilities (industry wide) have been rising since 2009. Application (e.g. Flash and Java) have risen drastically in H1 2012. Note that the rise affects non-Microsoft products, while Microsoft vulnerabilities have been reducing in number since H2 2010 (down 56.1%).
Exploits
HTML/Javascript (dropping in this period) and Java (rising since Q3 2011) lead the way, by a long shot.

Java has made a lot of bad security headlines in recent months and you can see why this is a concern. This is compounded by Oracle’s infrequent releases and their intransigence on this matter until the media as a whole said that Java needed to be turned off or removed.
Documents were the number 3 type to be hit. Guess who cam in at number 1 with no one in the rear mirror? You guessed it: Adobe Reader and Acrobat.
As for OS being attacked, Windows was the clear number 1, as it should be because it is on 95% of all PCs after all. Android is number 2. Apple are barely a spec on the market and were just bundled into the flat Others category.
The number 1 most attacked vulnerability was the 2 year old (August 2010) MS10-46 (made famous by Stuxnet but Ramnit is the #1 threat [and rising]).
Turns out that some of the jailbreak solutions for Android contain malware. Not too surprising, really.
Security Update Maintenance
No surprises here unfortunately:

Windows is still not being updated. I still encounter reasonably large organisations that “manually” approve patches. If you attend any presentation that I do that includes the topic of patching, then you know that manual approval is an oxymoron. These are usually the same people that have been hit by Conficker, etc, years after the patch to block it is released. That’s professional negligence in my opinion, pure and simple.
The lack of compliance for Adobe and Java is far some surprising. 28% percent of Adobe Reader users had not updated in 2 years. Adobe needs to do more to work with the OS vendors to get their products updated. And we all know that Java apps are usually written to run on a specific 5 year old version of the runtime, and that’s usually government (taxation) or banking software … you know … the stuff that needs the best security?!?!?!
Geography
Infection rates (FakePav fake malware – detections up 45 times) went up by 32.6% in the USA during Q1 and Q2 of 2012. Similar with Korea (Pluzoks trojan). Chine has a slight increase and everyone else was down.
Successful infection rates are rocketing in Korea. I mean rocketing.
Operating System
Windows XP SP3 leads the way. Windows 7 SP1 x86 is half of that rate, and the x64 is one third of it. Adware is dropping since Q1 2011 but Trojans are on the rise since Q2 2011.
Business Versus Home PCs
A Javascript threat called IframeRef number one threat on domain-joined (business) PCs. Here is the bit that is the most sickening and annoying of all. Conficker is still the number 2 threat on business machines. Seriously!?!?!!? The patch (MS08-067) to prevent this was released in October 2008 … 4 frakking years ago! Why the hell are businesses not patching? The tools have been freely available since … jeez 2003 or something when SUS was released!?!?! There is absolutely no legitimate excuse for this … don’t bother posting any lame excuses you might have to excuse your lack of professionalism if this applies to you; you’ll only highlight you own deficiencies for the world to see.
On the home side, Conficker is not in the top 10. KeyGen is the #1 and Autorun is #2.
Phishing Sites
Remember I said these guys want to steal money? All categories (including social media) are down, except for financial phishing (fake emails from your bank saying you need to log in to a dodgy site) are on the increase in Q2 2012. USA, Ireland, China, east Africa, south Gulf, and southeast Asia are all hotspots for this activity.
Go have a read of the document for yourself, especially if you are involved in the decision making of IT security or engineering in your site or those of your customers. It’s useful to see what’s going on right now so you can plan accordingly.
Technorati Tags:
Security